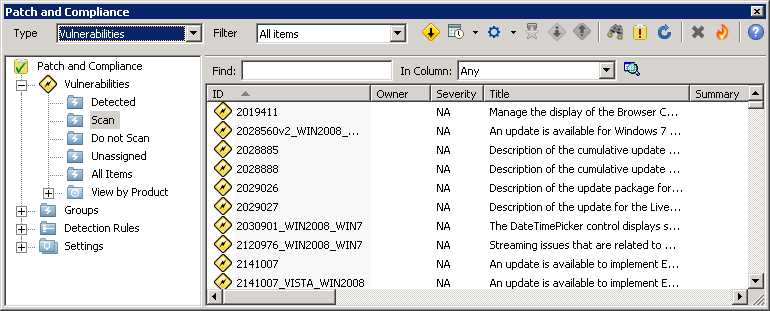
Viewing the security vulnerabilities listing and details - Documentation for BMC Network Automation 8.9 - BMC Documentation
Adventures in Automation: Introduction to Vulns, Common Vulnerabilities and Exposures, the CVE List, and the National Vulnerability Database

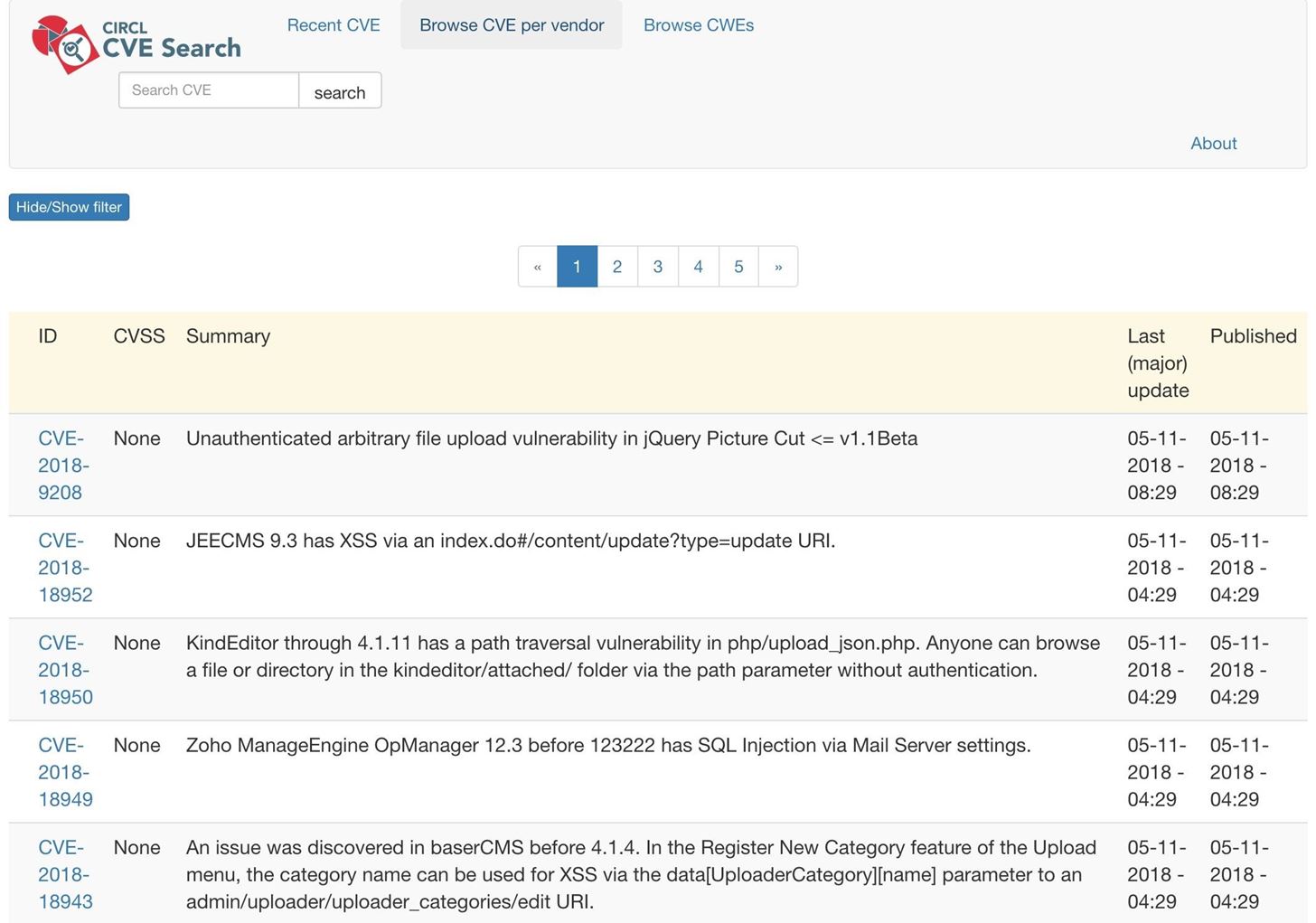
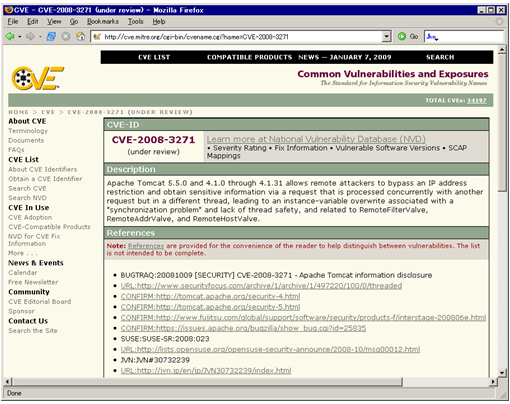
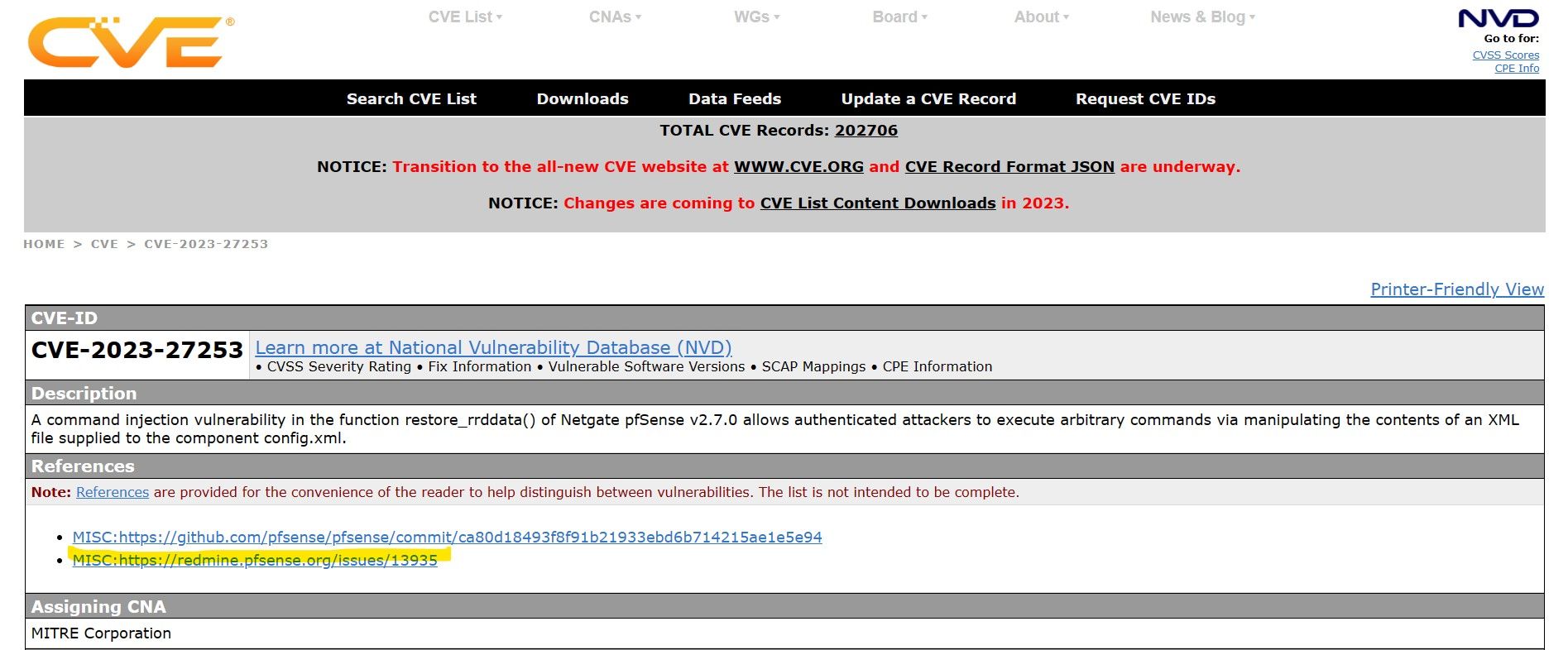
Example CVE from cve.mitre.org Each CVE includes metadata such as a... | Download Scientific Diagram
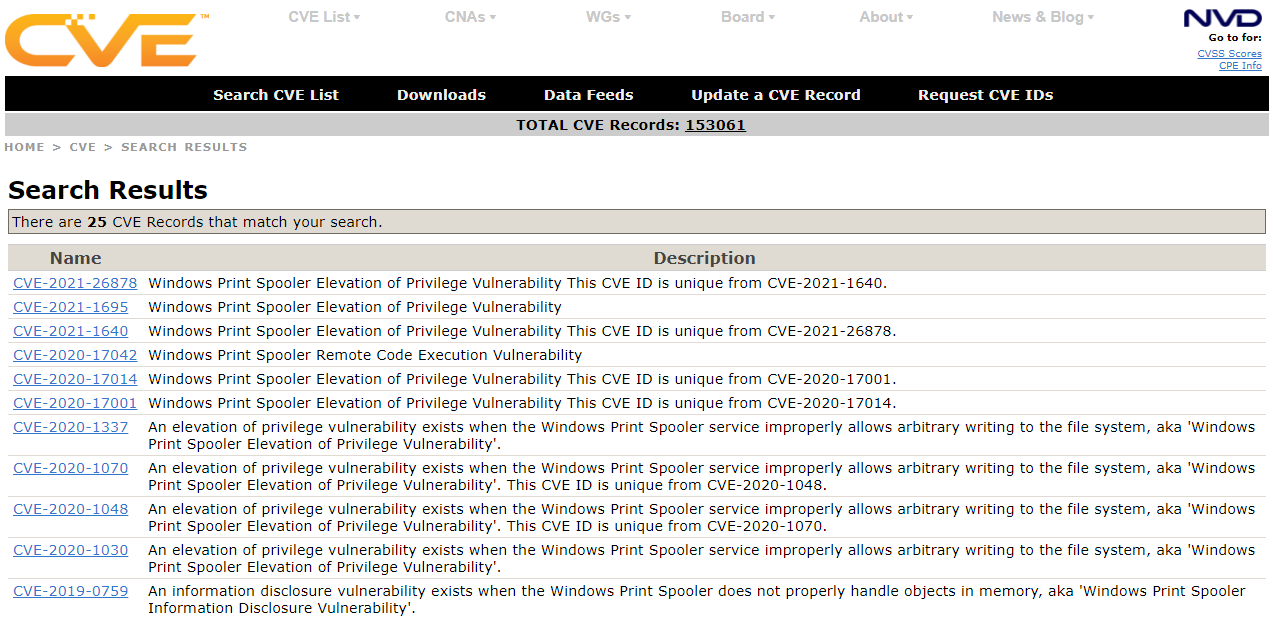

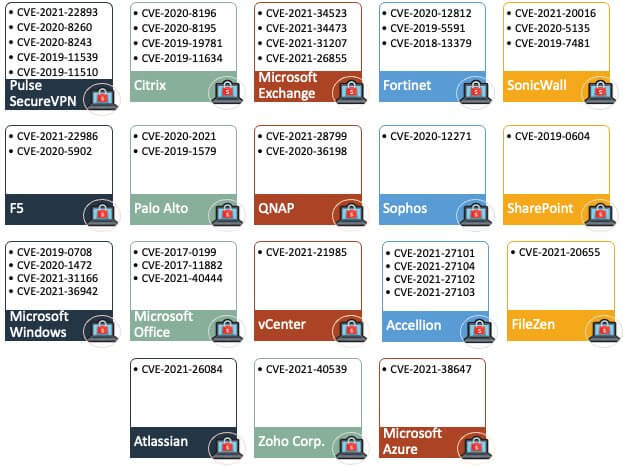






.png)